Products
Buy options
€5.00Please check product and platform compatibility before placing an order
All pictures shown are for illustration purpose only. Actual product may slightly vary due to product enhancement or other reasons.
USB-A to Lightning adapter
Looking to use your FIDO2 USB-A key with your iPhone or iPad ? You'll need our FIDO2 USB-A to Lightning adapter to make it happen! This adapter is specifically designed to connect your FIDO2 USB-A key to your iPhone or iPad's Lightning port, enabling secure and convenient authentication for your iOS device. With its durable construction and easy-to-use design, our adapter ensures a seamless experience every time you need to authenticate with your FIDO2 key.
Additionally, there is another aspect that appears to be more of an iOS GUI glitch. When an iPhone prompts the user to choose the passkey type, users should start using the FIDO2 key without following the on-screen instructions.

We understand that security is a top priority for our customers, and we want to ensure that you have all the information you need to make an informed purchase. If you have any questions or concerns about our adapter or your FIDO2 key, please don't hesitate to contact us.
Blog
03-03-2025
Understanding Entra’s New Time Drift Allowance
 Microsoft Entra has recently updated its time drift allowances for TOTP, reducing the window to approximately 2 minutes. This change may impact users of hardware tokens that have not been used for an extended period.
Microsoft Entra has recently updated its time drift allowances for TOTP, reducing the window to approximately 2 minutes. This change may impact users of hardware tokens that have not been used for an extended period.
29-01-2025
Beware of the Passkey Dialog: Not All Options Are FIDO2 Security Keys
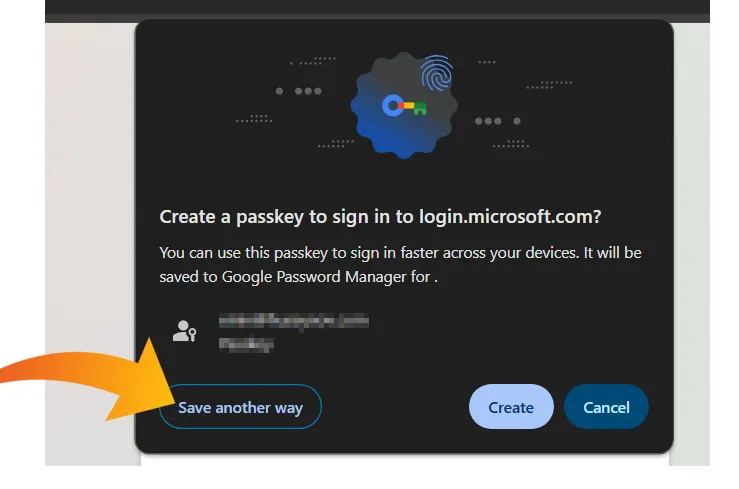 When setting up a passkey on Windows, the standard authentication dialog often presents multiple options for storing credentials.
When setting up a passkey on Windows, the standard authentication dialog often presents multiple options for storing credentials.
09-01-2025
PIN+ Key Series Achieves FIDO Level 2 Certification
 We are thrilled to announce that our PIN+ Key Series has officially obtained FIDO Level 2 (L2) Certification, a significant milestone that underscores our commitment to delivering the highest level of security for our users.
We are thrilled to announce that our PIN+ Key Series has officially obtained FIDO Level 2 (L2) Certification, a significant milestone that underscores our commitment to delivering the highest level of security for our users.




















